Modern authentication mechanisms for web application
Authentication: Process of verifying the credentials of a user or device attempting to access a restricted system. It verifies the user. In simple words, Authentication is (Who are you?)
Authorization: Process of verifying whether the user or device is allowed to perform certain tasks on the given system. It checks the privileges of the user. In simple words, Authorization is (What can you do?)
Prior to authorization, there is authentication. Prior to receiving access to resources based on their authorization level, a user’s validity must be established. Once authenticated, they are given roles like admin, moderator, etc. that provide them access to the system’s specific features.
Different methods of Authentication:
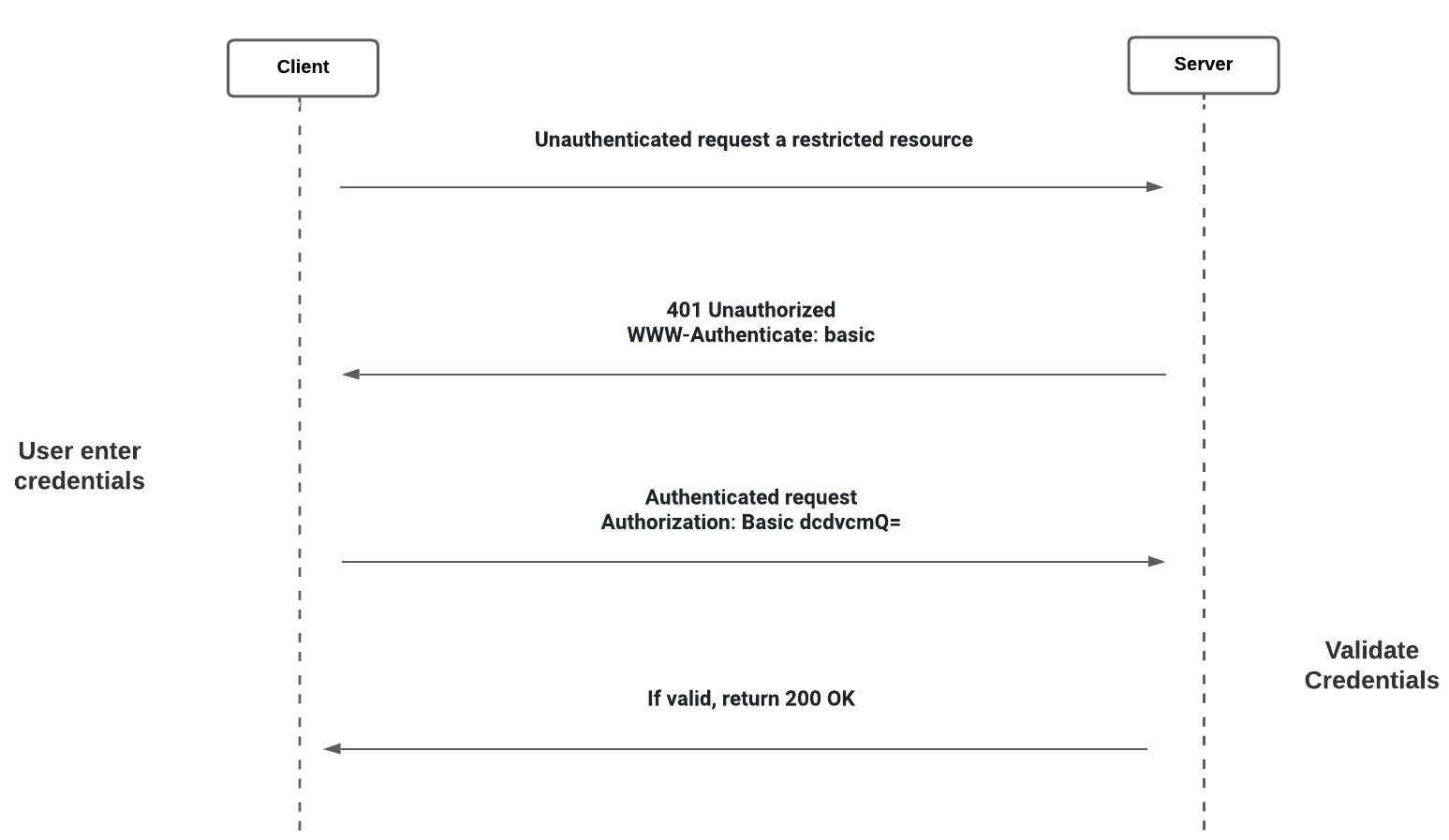
HTTP Basic Authentication:
- A basic form of authentication built into the HTTP protocol.
- In this login credentials are sent in request headers with each request.
- The credentials are not encrypted. Instead, they are concatenated together with a : to form a single string. Then the whole string is then encoded using base64.
- This method is stateless i.e., the client must supply the credentials with each request.
Pros:
- Easy to implement.
Cons:
- Poor security feature because Base64 is not the same as encryption. It’s just another way to represent data and can be decoded easily.
- Credentials must be sent with every request.
- User can only be logged out by rewriting the credentials with an invalid one.
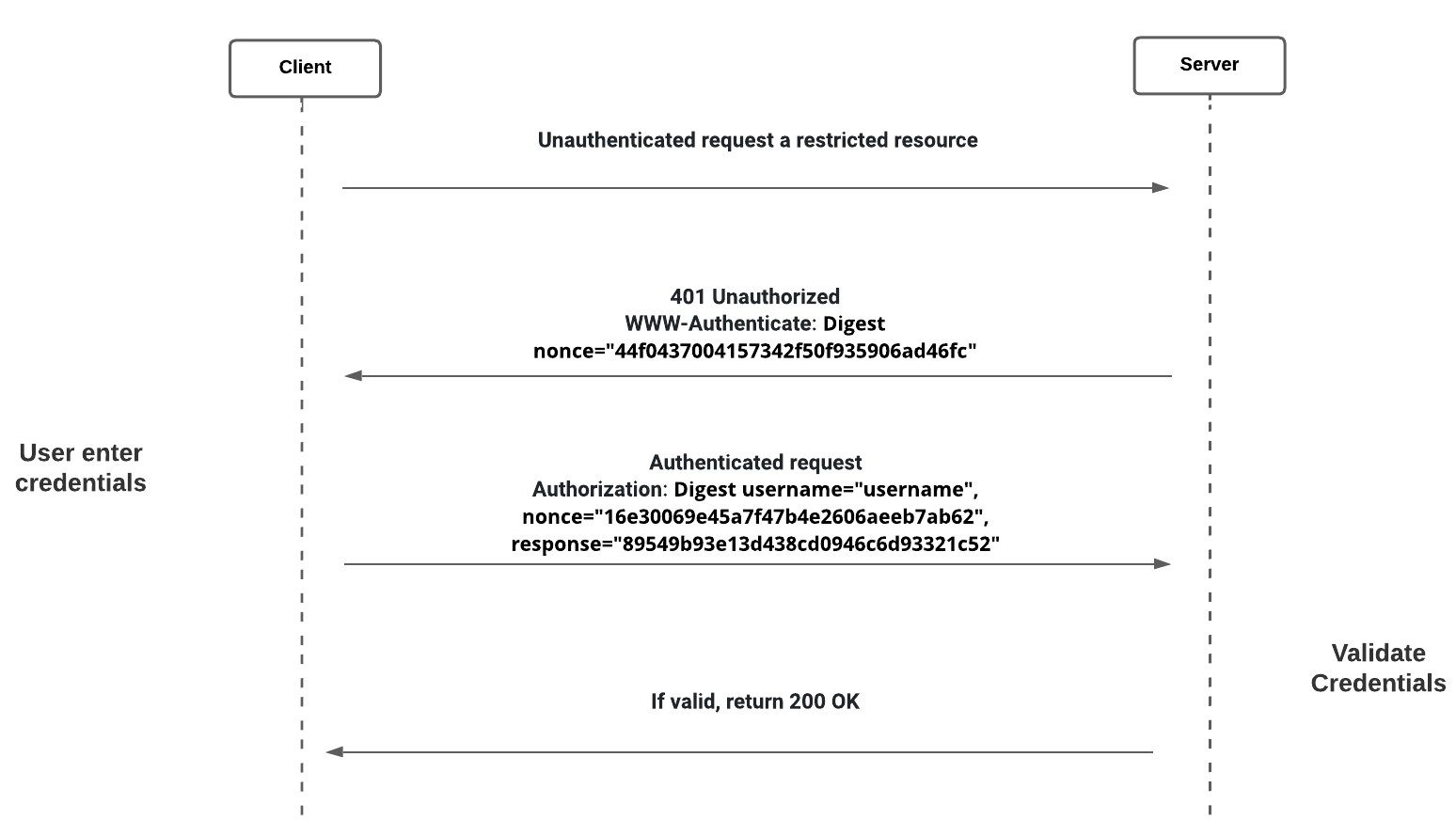
HTTP Digest Authentication:
- More secure form of HTTP Basic Auth.
- The main difference is that the password is sent in MD5 hashed form rather than in plain text.
Pros:
- More secure than Basic AUTH since the password is not sent in plain text.
Cons:
- Credentials must be sent with every request.
- User can only be logged out by rewriting the credentials with an invalid one.
- Vulnerable to man-in-the-middle attacks.
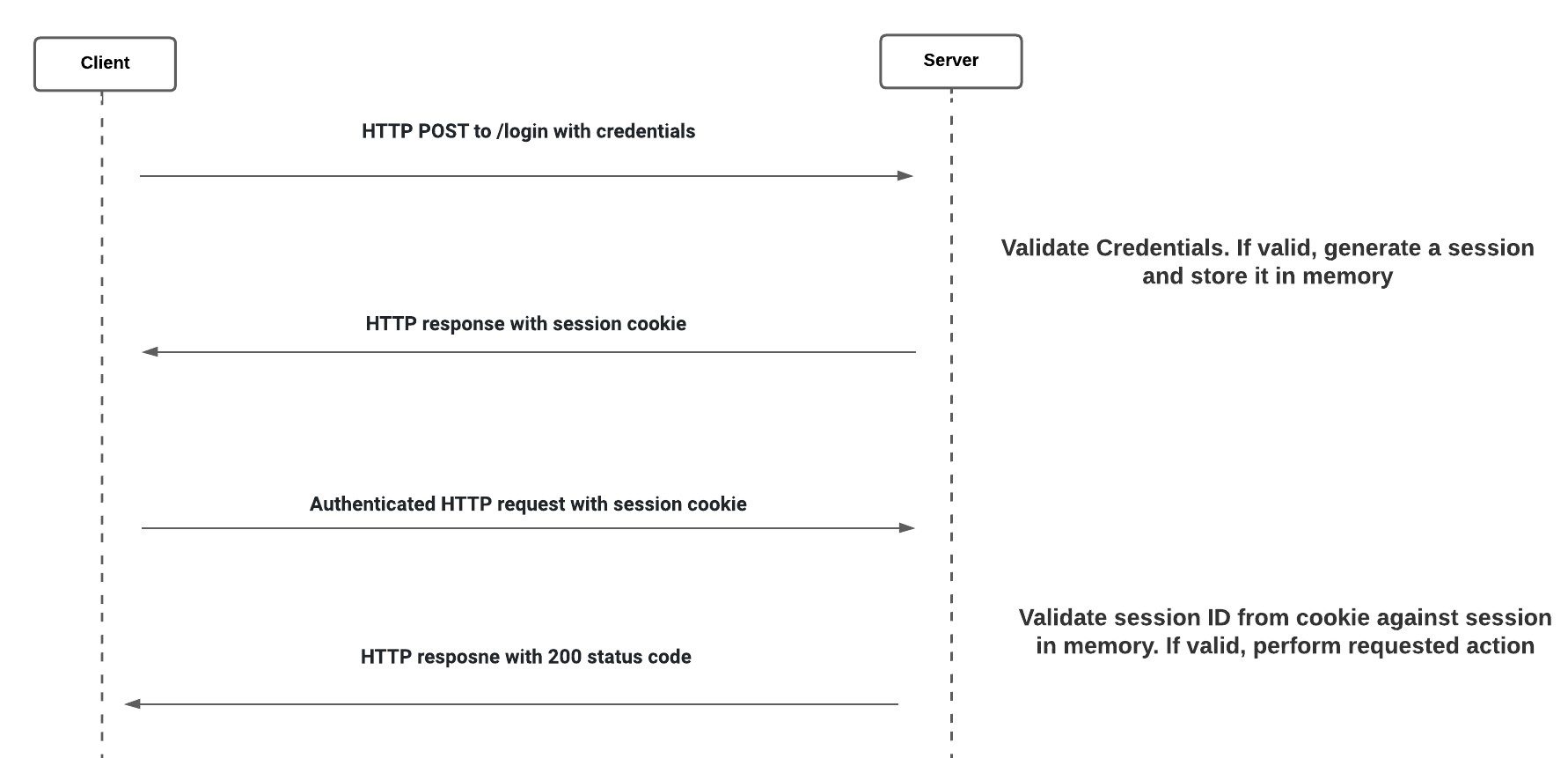
Session-based Authentication:
- In session-based authentication the state of the user is stored on the server and doesn’t require the user to provide credentials with each request.
- When a user logs in, the credentials are validated by the server. If they are valid, the server creates a session and stores it in the session store, and the session ID is sent back to the browser.
- This session ID is stored by the browser as a cookie, which is sent each time a request is made to the server.
- Session-based is stateful. Each time a client makes a request to the server, it looks up the session in memory to link the session ID to the relevant user.
Pros:
- Credentials are not required with each request.
Cons:
- The user session information is stored in the session store that needs to be shared across multiple servers to enable authentication. Due to this, it doesn’t work well for RESTful services as REST is a stateless protocol whereas session-based authentication is stateful.
- Cookies are being sent with each and every request even if it doesn’t require authentication.
- Vulnerable to CSRF attacks.
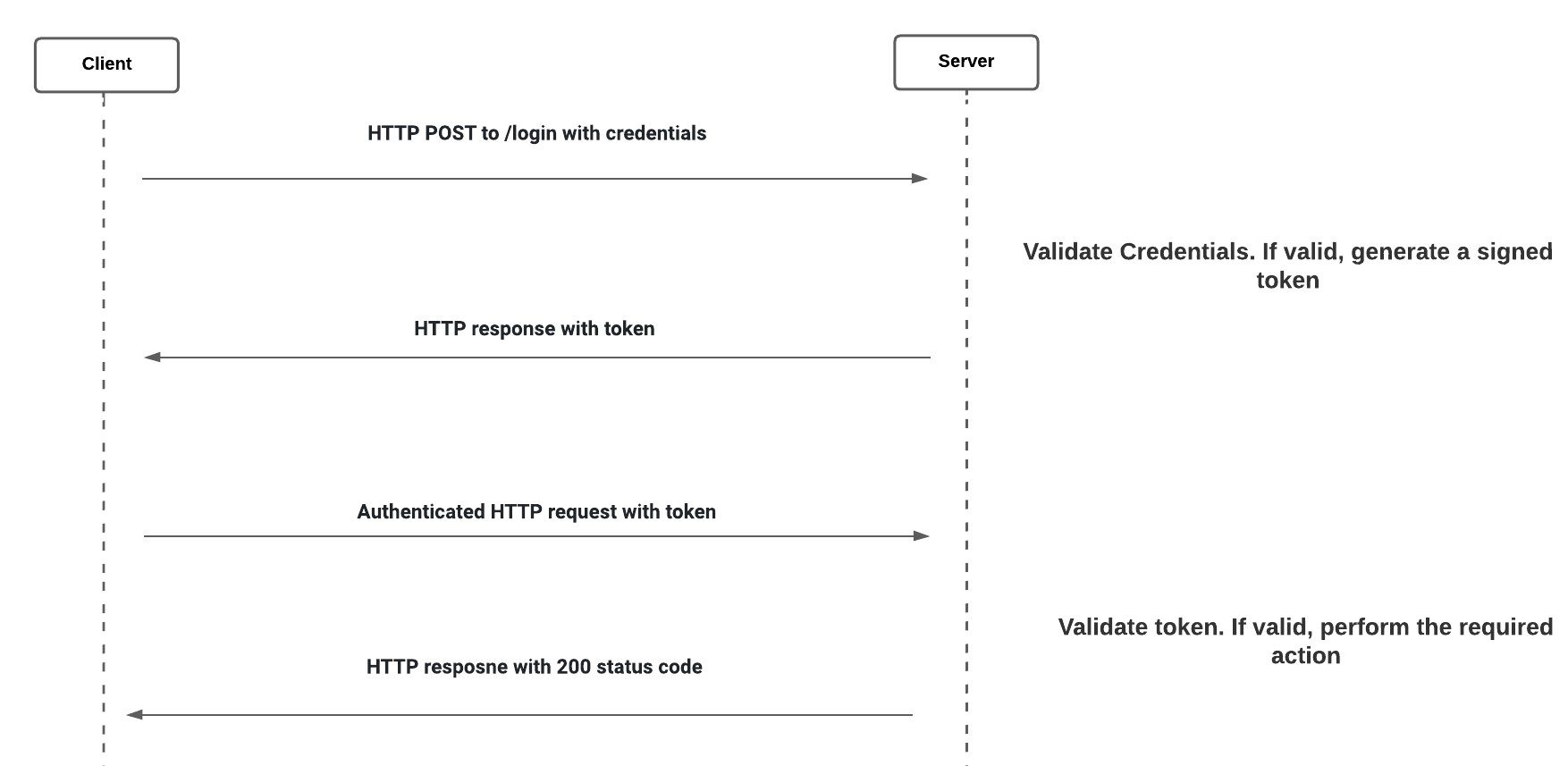
Token-Based Authentication:
- It uses tokens to authenticate users instead of cookies. The user authenticates using the valid credentials and the server returns a signed token. Then this token can be used for subsequent requests for a limited time period.
- The most used is a JSON Web Token which consists of three parts:
- Header: Includes the token type and hashing algorithm used.
- Payload: Includes the claims which are statements about the subject.
- Signature: Used to verify that the data wasn’t changed.
- All these three are encoded using base64 and concatenated using a . and hashed. The token is authenticated using a signature which is signed with a secret private key.
- These tokens don’t need to be saved on the server side. They just need to be validated using their signature.
Pros:
- It’s stateless. The token can be verified using the signature; thus the server doesn’t need to store it. As database search is not necessary, this speeds up the request.
- Suited for a microservices architecture, where multiple services require authentication at a single time. Only handling of the token and the token secret at each end needs to be configured.
Cons:
- You cannot delete tokens. They can only expire. This means that if the token is somehow leaked, a hacker might use it maliciously until it expired. Therefore, it’s crucial to set the token expiry timer to a relatively short amount of time, like 15 minutes.
- Refresh tokens must be configured to issue new tokens automatically when they expire.
Multi-Factor Authentication:
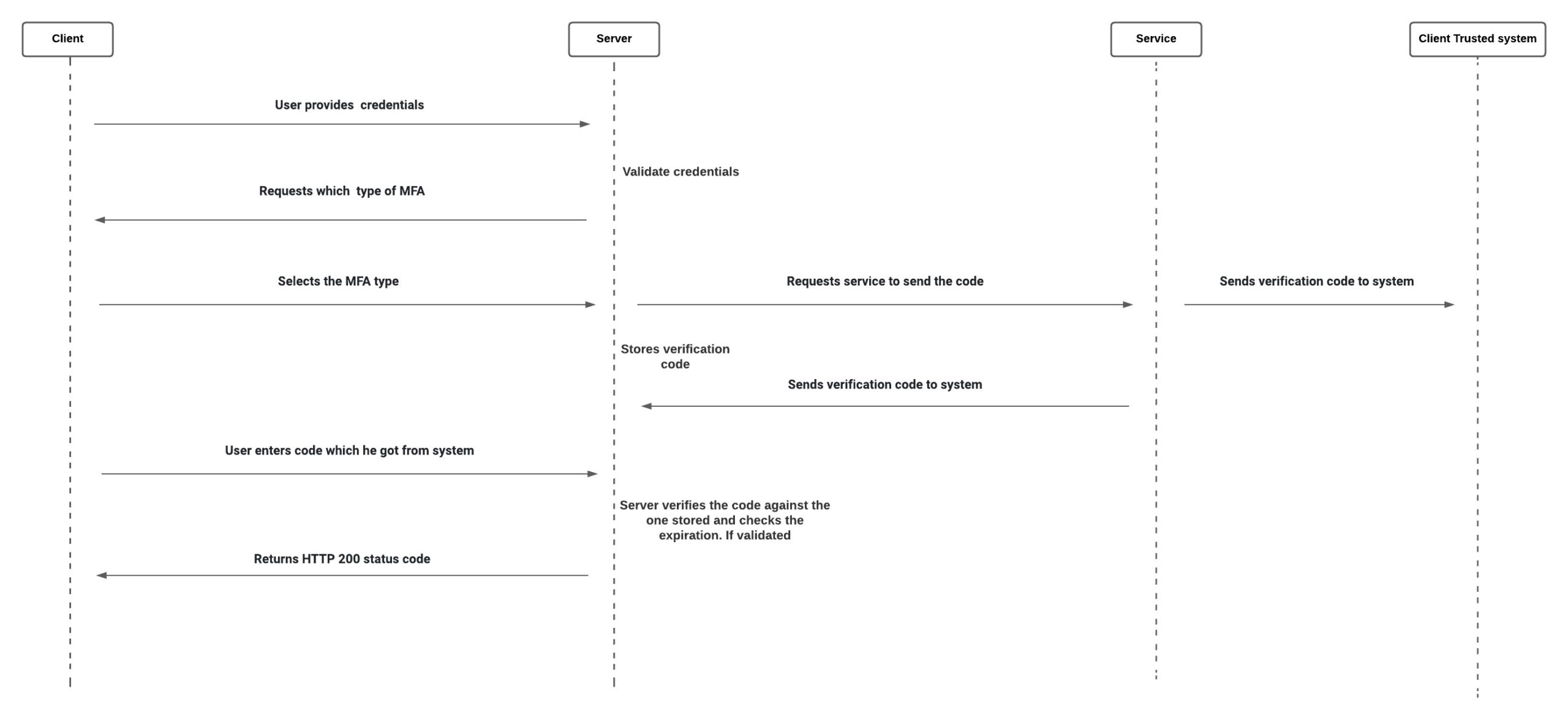
- (MFA) is a type of authentication in which a person needs to successfully pass numerous factors to access a service or network.
- It’s an additional security measure on the top of the typical password-based login. Along with their credentials, users must additionally provide a second factor in the form of a one-time code or push notification that they will receive through phone or email.
- Examples include codes generated from the user’s smartphone, Captcha tests, fingerprints, voice biometrics, or facial recognition.
- To use MFA a trusted system should be present like a phone number or an email. The code is sent to that system and the user enters the code into the service if they match then the user is said to be verified.
- They are stateless i.e., they can be verified with multiple methods.
- MFA is recommended for apps that involve highly sensitive data.
Pros:
- Adds an extra layer of security.
- There is no risk that a stolen password can be used on several websites or services that utilize MFA.
Cons:
- When the trusted device is unavailable, issues occur (dead battery, network error, etc.)
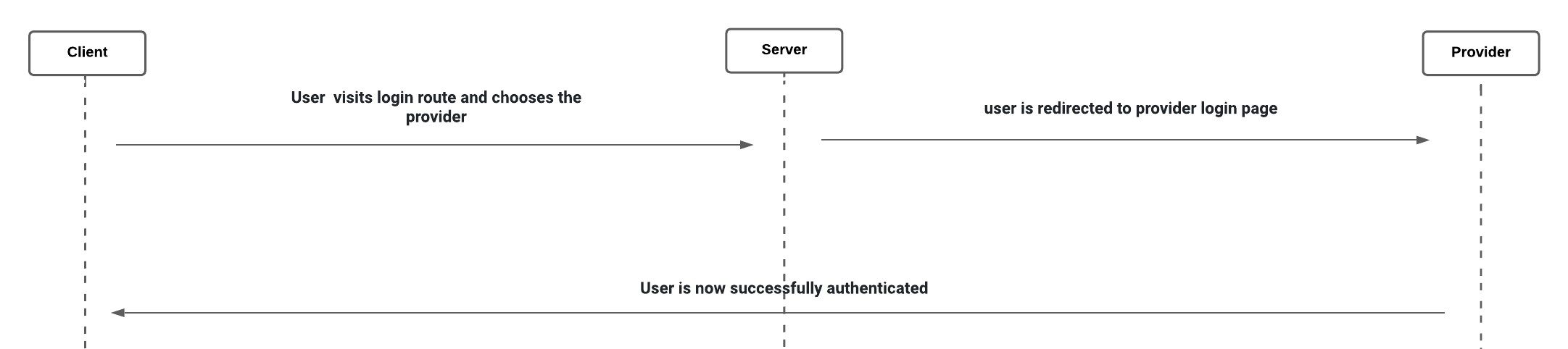
OAuth and OpenID:
- Used to implement social login, a type of single sign-on (SSO) that lets users sign in to third-party websites using their Facebook, Twitter, or Google accounts without creating new login accounts just for those websites.
- This method is often coupled with session-based authentication.
Pros:
- Improved security.
- Login processes are simpler and quicker because a username and password don’t need to be created or remembered.
- Due to password-less authentication, there won’t be any harm to third parties in the event of a security breach.
Cons:
- Your application depends on another app, outside of your control. If the system is down, users won’t be able to log in.
- Your application won’t be accessible to users who don’t have accounts with the configured OpenID providers. The best strategy is to use both — for instance, username and password and OpenID — and provide the user the option of selecting one.
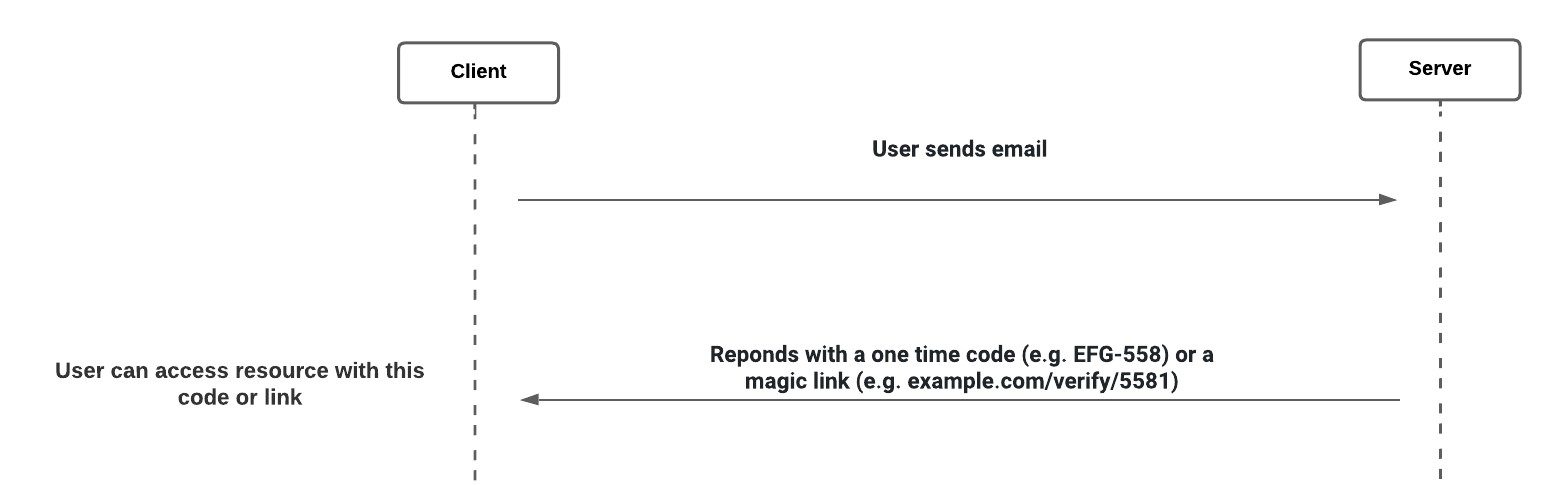
Password-less Authentication:
- A part of multifactor authentication or combined with single sign-on (SSO).
- User only provides email, and the server sends the user a one-time code or a link to access the resource.
Pros:
- Reduces complexity.
- Flexible and easy to use.
- Strong security
Cons:
- Potentially increased costs.
Biometric with (Web-Authentication):
- Biometric authentication is a security process that relies on the unique biological characteristics of individuals to verify they are whom they say they are.
- Biometric authentication systems compare physical or behavioural traits to stored, confirmed, authentic data in a database.
- Biometric identification uses biometrics, such as live pictures, fingerprints, and retina scans, to identify a person, whereas biometric authentication is the use of biometrics to verify people are whom they claim to be.
- Biometric data is given to the device instead of a password and it generates public and private keys. Private remains on device whereas public is on server, and both are compared for verification.
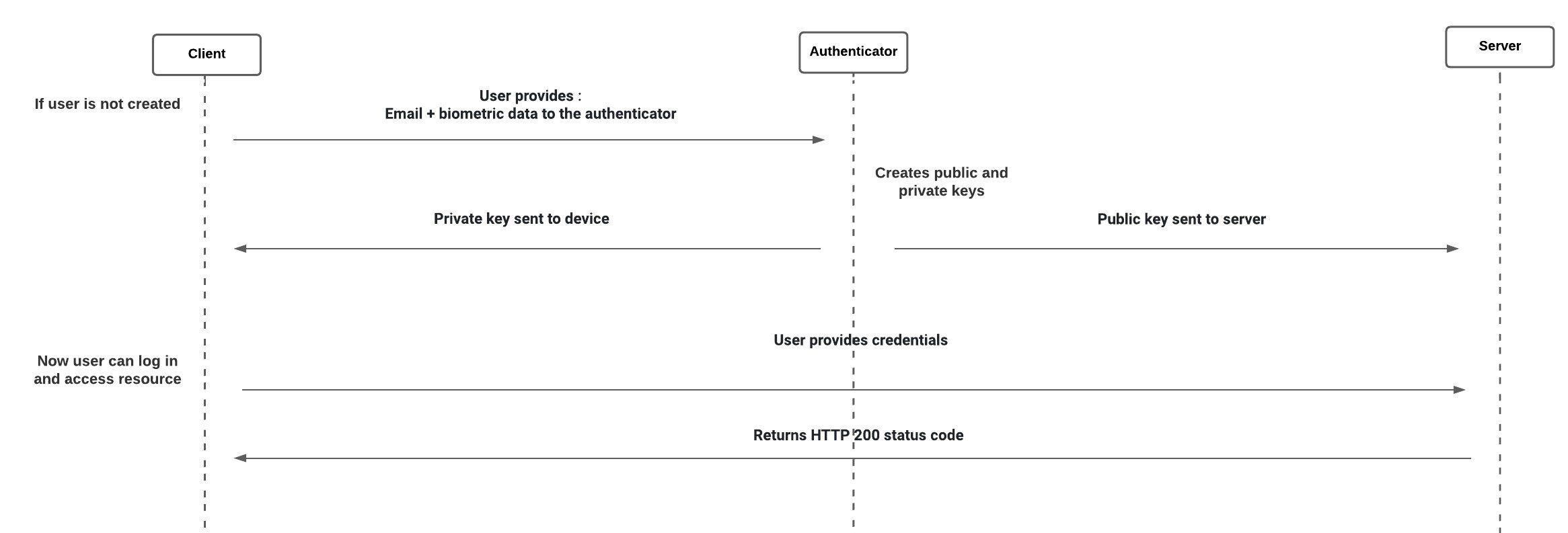
Pros:
- It provides safety and is non-transferable.
- It also recognizes distinct characteristics.
- It is very easy to use and very safe.
Cons:
- Currently there is a lack of accuracy which can lead to the failure of the biometric system.
- At times errors in biometric devices appear like false rejection and acceptance.
Certificate-based Authentication:
- Digital certificates are used in certificate-based authentication solutions to identify individuals, machines, or devices. A digital certificate is an electronic document that is based on the idea of a passport or a driver’s license.
- A certificate consists of a user’s digital identity, which includes a public key and the digital signature of a certifying authority. This certificate demonstrates that the public key and the certificate’s issuer are both the same person.
- When logging into a server, users give their digital certificates. The server checks the validity of the certificate authority and the digital signature. The user’s ownership of the proper private key that goes with the certificate is then verified by the server using cryptography.
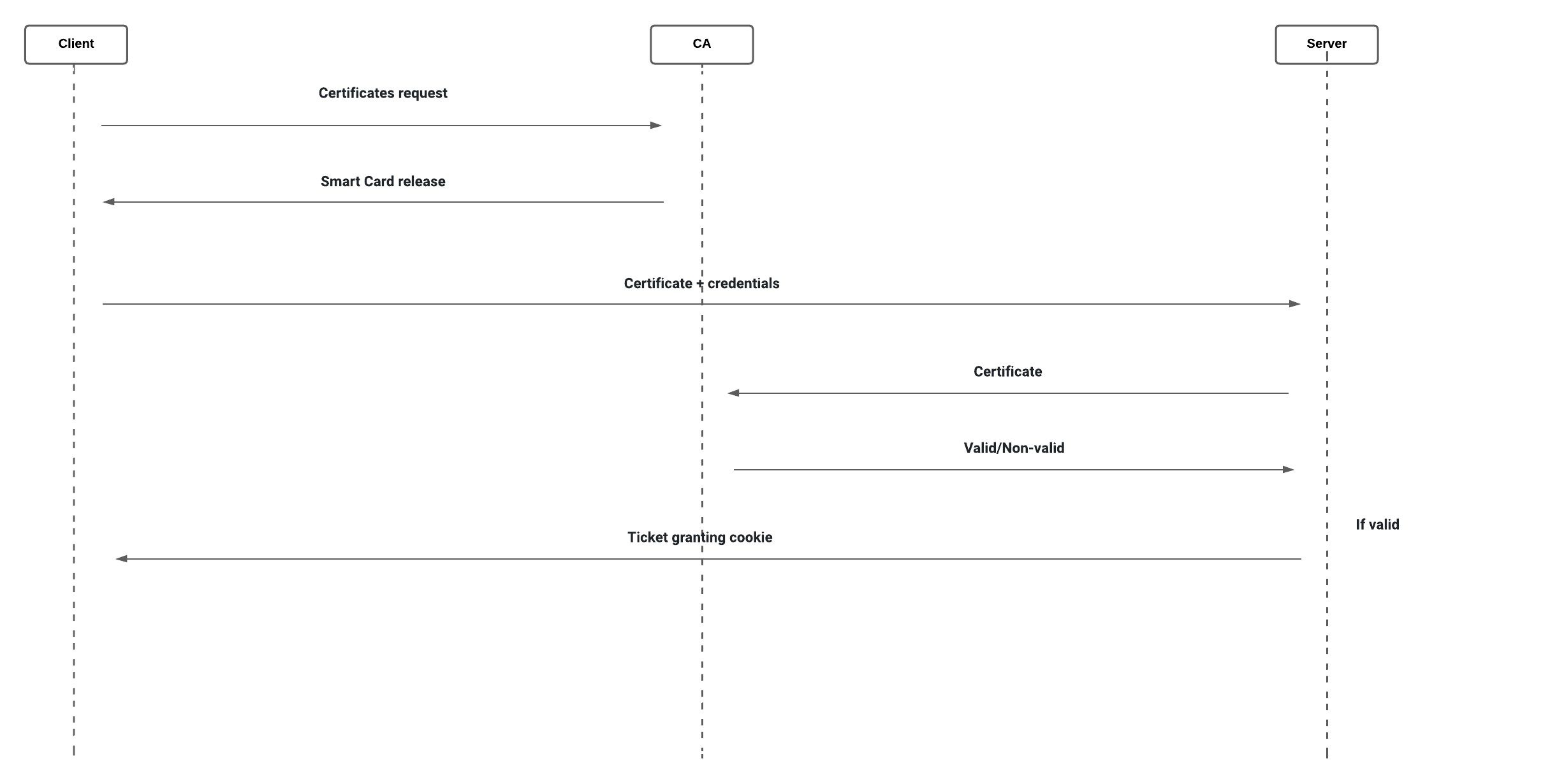
Pros:
- Removes password-related problems such leaks, hackers, and weak passwords.
- Combined with a username and password validation, it offers a safe authentication technique.
Cons:
- The certificate must be protected by the user.
- For first-time users, installation might not be as simple.
- It is necessary to correctly distribute certificates and associated private keys.
Conclusion:
There are several different web authentication methods, all of which have their own pros and cons. The usage of them depends on your scenario. The basic rules are:
- Session-based authentication is the most suitable method for web applications that make use of server-side templating.
- Token-based authentication is advised for RESTful APIs because it is stateless.
- If you are dealing with highly sensitive data, you might consider including multifactor in your authentication procedure.
Please share your kind feedback in the comments section. For any query, feel free to Contact us or email us on [email protected]
October 3, 2022 | Written by: Bilal Ul Haque